BitLocker Recovery Key Retrieval Methods
There will likely come a time when you will need to retrieve a BitLocker Recovery Key. The reasons you may need to recover it can vary. Personally, I've experienced an assortment of needs for the BitLocker Recovery key. The commonality between each experience, however, typically stems from a hardware issue. I've witnessed the need to retrieve the key occur when a motherboard was replaced, a Bios update was run and even when a laptop was stolen.
In the past, if an end user needed to retrieve their BitLocker Recovery Key, they'd typically have the call in to IT. That's not necessarily the case anymore if they are listed as the owner on the device in Azure AD (Active Directory). If this sounds like your situation, you can check out how to recover the key in section 1.3 below.
If you are an administrator, you will likely get a number of requests for the key regardless of the Self-Service Portal's capabilities. In this instance, there are two approaches to retrieve your BitLocker Recover Key. This first being through Endpoint Manager and the other through Azure AD. You can follow the instructions below step-by-step to get the key.
1.1 Endpoint Manager
-
Log into Endpoint Manager and search for the device by selecting "Devices", "Windows", and then entering the device name or serial number. Once the device appears click on it.
2. In the left pane, select "Recovery keys".
3. Select "Show Recovery Key". Note: If there is more than one entry, use the "BITLOCKER KEY ID" to select the correct "BITLOCKER RECOVERY KEY".
4. The following screen will appear with the BitLocker Recovery Key.
1.2 Azure AD
5. Log into Azure Portal and select the Azure Active Directory blade, search for the device by entering the device name or serial number in the search box (1). When the device is found select it to open the record (2).
6. Select Show Recovery Key". Note: If there is more than one entry, use the "BITLOCKER KEY ID" to select the correct "BITLOCKER RECOVERY KEY".
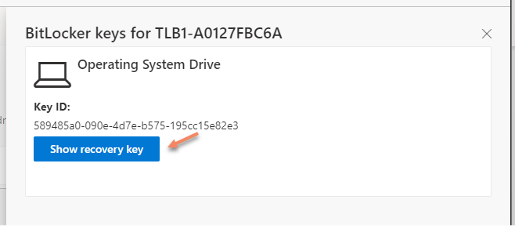
1.3 Self-Service Portal (End user can access if they are listed as an "Owner" of the device in Azure AD).
7. Log into the Self-Service Portal and select "Devices".
8. Select the drop-down arrow next to the device in question.
9. Select "View BitLocker Keys".
10. Select "Show recovery key"
11. A window will appear in the middle of the screen with the BitLocker Recovery Key.
Tom Bernardini
Tom is our Modern Work & Security Engineer in the US, based out of South Florida. Having worked most of his 15 years in the IT industry in the medical sector, he was first introduced to the MDM/MAM while working at BlackBerry. Along with his experience working for an MSP (Managed Services Provider), Tom has a strong focus on clients' business needs, both large and small.
Host Jana Axline and Mobile Mentor Founder, Denis O'Shea, discuss tactics for successfully balancing corporate security with employee experience. The two examine the change in the way employees work as a result of the pandemic and remote work. They also deep dive into the recent power shift between employer and employee.
On the surface, Windows 365 and Azure Virtual Desktop look like a similar product. Both deliver an excellent virtual experience for end-users, but when you look closer, there are some glaring differences between the two tools. Microsoft created these two solutions for different use cases, and the differences address the scale of complexity that exists in one business versus another.
Windows 365 Cloud PC is one of many highly intelligent tools Microsoft has rolled out in the recent past. Windows 365 comes in both Windows 10 and Windows 11, and is yet another tool for modern work in a climate that continues toward hybrid and remote work.
Traditionally, Managed Service Providers (MSPs) have operated with an on-premises strategy: local servers for files, print, and accounts with employees and their machines mostly in the building. Known as the "castle-and-moat" strategy, it relied on keeping everything good inside and everything bad out. This model was effective in the past, but as COVID-19 has ushered in a new era of hybrid and remote work – this strategy is no longer fit for purpose.
Microsoft used the lessons learned from secure-core PCs and applied them to the new Windows 11 operating system. The secure-core PCs were initially developed for highly focused sectors like financial services, government, and healthcare to protect sensitive data.
Microsoft Defender has evolved significantly in recent years, not only as a product, but also as an ideology for keeping your environment secure.
Mobile Mentor Founder, Denis O'Shea, discusses with the Influential Personal Brand Podcast host, AJ Vaden, the move to remote work since the beginning of the pandemic. The two explore the consequences of the shift concerning the way employees behave and work by examining the results of the recent 2022 Endpoint Ecosystem study.
Mobile Founder, Denis O'Shea, discusses where security and employee experience intersect with the #WorkTrends podcast host, Meghan Biro.
Like everyone, Government workers endured a rapid digital transformation in recent years. This has shifted the way many agencies operate and as a result, the needs and priorities of front-line employees have evolved over the past two years as well.
Healthcare workers are among the most impacted employees of the pandemic. Overcrowded hospitals, increased hours, burnout, and staff shortages have menaced the industry over the past two years. The pandemic brought a rapid digital transformation in the industry and the shift impacted the way Healthcare workers operate.
Mobile Mentor CEO, Daniel McCarthy and NZ Head of Sales, Jared Pederson, discuss with host, Nadia Phillips, how the pandemic has accelerated BYOD (Bring Your Own Device) technology when it comes to onboarding new employees. The three also deep dive into the methodology behind Zero Trust and outline the tools necessary to build a Zero Trust Architecture.
For small businesses to large enterprises, the Health Dashboard is the single place to gather information and take action on sync app adoption and health. The Health Dashboard is a great feature for admins looking for a high-level view of how OneDrive is working for their team.
Configuring a boilerplate Chrome homepage can help you to avoid a lot of these redundant questions. By adding links to resources like a company portal or SharePoint, users will be reminded of where company assets live each time, they fire up their browser. It's easily achievable with Intune.
Mobile Mentor founder, Denis O'Shea, and Intel's Chief Solutions Architect, Darren Pulsipher, discuss the challenges and solutions associated with onboarding remote workers in a post-pandemic world.
As an administrator, there's likely going to be a time where you will need to restrict certain apps from accessing your network on particular devices. It's not an uncommon practice and the need to block apps is more often than not stems from data security needs.
Mobile Mentor Founder, Denis O'Shea, and Karen Clauss discuss navigating the right balance between security and employee experience in this episode of iHeart's The Art of Improvement podcast. The two deep dive into concepts and strategies that empower workers and help to secure the modern workforce.
The pandemic forced digital transformation onto the world in 2020. Business continuity emergency plans were implemented – some fared better than others. The Endpoint Ecosystem study takes a critical look at regulated industries that jumped ahead of the curve in terms of security and employee experience and why others fell behind. In this article, we examine how the Finance Industry stacks up.
Over time, Azure AD can begin to collect stale devices within its platform. This can happen for a variety of reasons, one cause we recently encountered stemmed from non-persistent VDI machines creating device registrations on end user's O365 licenses.. In this example, every time their machine spun up, Azure AD would create a new registration for a user's account.
Have you ever needed to configure your entire group's chrome settings for security purposes or to meet company preferences? It's not uncommon for companies to do so to keep their team aligned. Many groups may want to add or block particular extensions in Chrome for productivity reasons. For Intune admins, there is a relatively simple set of instructions to achieve your desired outcome with Chrome configurations.
There will likely come a time when you will need to retrieve a BitLocker Recovery Key. The reasons you may need to recover it can vary. The commonality between each experience, however, typically stems from a hardware issue.
The Education industry has perhaps experienced more disruption than any other during the pandemic. Governments have poured money into schools over the past two years to support the continued education of students.
Navigating the trade-off between endpoint security and employee experience has always been challenging but it has become critical in this post-pandemic world. We can point to the Endpoint Ecosystem (the combination of the devices, apps, sign-in process, and support experience) as a barometer of the modern workforce. When a company's Endpoint Ecosystem works well, employees are secure, productive and happy.
It's simple. Companies who have embraced Modern Endpoint Management have more proactive IT teams than their peers who use legacy endpoint practices. This is because they have time to plan ahead, and they are not always fighting fires.
To clear some of the confusion, there are two concepts you'll need to understand. Azure AD joined (AADJ) and Azure AD registered (AADR). This guide ultimately focuses on how to properly Azure AD join a device, but you'll first need a breakdown of the difference between AADJ and AADR.
In a modern cloud environment, app patching has changed for the better. Patch Tuesday is now largely a concept of the past. IT teams are now able to push patches and upgrades over the air with ease - rectifying security vulnerabilities in real time. The duration of time between discovering a security vulnerability and patching it has been reduced drastically with Modern App Patching.
At Mobile Mentor, we use Microsoft flow a lot. Recently, I have created automations to trigger when Forms are submitted, to create approval flows and complete logic for simple business processes. However, I had not previously considered automation for personal productivity gains.
Zero Touch Provisioning eliminates the time-heavy effort that legacy device configuration methods require. Zero Touch gives IT departments the ability for users to self-provision devices remotely, without IT ever having to physically touch the devices.
griffinealsong.blogspot.com
Source: https://www.mobile-mentor.com/insights/bitlocker-recovery-key-retrieval-methods









































0 Response to "Intel Enter the Recovery Key to Get Going Again"
Post a Comment